Where can I get ISC Cissp exam certification tips? Latest Cissp exam dump, Cissp pdf, And online hands-on testing free to improve skills and experience, 98.5% of the test pass rate select lead4 through Cissp dump: https://www.leads4pass.com/cissp.html (latest update)
ISC Cissp exam pdf free download
[PDF Q1-Q13] Free ISC Cissp pdf dumps download from Google Drive: https://drive.google.com/open?id=126N3hMXNUbmXmHWw3T5OGRoE-aJ6vvmI
Real and effective ISC Cissp Exam Practice Questions
QUESTION 1
Physical security is accomplished through proper facility construction, fire and water protection, anti-theft mechanisms,
intrusion detection systems, and security procedures that are adhered to and enforced. Which of the following is not a
component that achieves this type of security?
A. Administrative control mechanisms
B. Integrity control mechanisms
C. Technical control mechanisms
D. Physical control mechanisms
Correct Answer: B
Explanation: Integrity Control Mechanisms are not part of physical security. All of the other detractors were correct this
one was the wrong one that does not belong to Physical Security. Below you have more details extracted from the
SearchSecurity web site:
Information security depends on the security and management of the physical space in which computer systems
operate. Domain 9 of the CISSP exam\\’s Common Body of Knowledge addresses the challenges of securing the
physical space,
its systems and the people who work within it by use of administrative, technical and physical controls. The following
topics are covered:
Facilities management: The administrative processes that govern the maintenance and protection of the physical
operations space, from site selection through emergency response.
Risks, issues and protection strategies: Risk identification and the selection of security protection components.
Perimeter security: Typical physical protection controls.
Facilities management
Facilities management is a complex component of corporate security that ranges from the planning of a secure physical
site to the management of the physical information system environment. Facilities management responsibilities include
site selection and physical security planning (i.e. facility construction, design and layout, fire and water damage
protection, antitheft mechanisms, intrusion detection, and security procedures.) Protections must extend to both people
and
assets. The necessary level of protection depends on the value of the assets and data. CISSP?candidates must learn
the concept of critical-path analysis as a means of determining a component\\’s business function criticality relative to
the
cost of operation and replacement. Furthermore, students need to gain an understanding of the optimal location and
physical attributes of a secure facility. Among the topics covered in this domain are site inspection, location, accessibility
and
obscurity, considering the area crime rate, and the likelihood of natural hazards such as floods or earthquakes.
This domain also covers the quality of construction material, such as its protective qualities and load capabilities, as well
as how to layout the structure to minimize the risk of forcible entry and accidental damage. Regulatory compliance is also
touched on, as is preferred proximity to civil protection services, such as fire and police stations. Attention is given to
computer and equipment rooms, including their location, configuration (entrance/egress requirements) and their
proximity to
wiring distribution centers at the site.
Physical risks, issues and protection strategies
An overview of physical security risks includes the risk of theft, service interruption, physical damage, compromised system
integrity and unauthorized disclosure of information. Interruptions to business can manifest due to loss of power,
services,
telecommunications connectivity and water supply. These can also seriously compromise electronic security monitoring
alarm/response devices. Backup options are also covered in this domain, as is a strategy for quantifying the risk
exposure by a simple formula.
Investment in preventive security can be costly. Appropriate redundancy of people skills, systems and infrastructure
must be based on the criticality of the data and assets to be preserved. Therefore a strategy is presented that helps
determine the selection of cost appropriate controls. Among the topics covered in this domain are regulatory and legal
requirements, common standard security protections such as locks and fences, and the importance of establishing
service
level agreements for maintenance and disaster support. Rounding out the optimization approach are simple calculations
for determining the mean time between failure and mean time to repair (used to estimate average equipment life
expectancy) — essential for estimating the cost/benefit of purchasing and maintaining redundant equipment.
As the lifeblood of computer systems, special attention is placed on adequacy, quality, and protection of power supplies.
CISSP candidates need to understand power supply concepts and terminology, including those for quality (i.e. transient
noise vs. clean power); types of interference (EMI and RFI); and types of interruptions such as power excess by spikes
and surges, power loss by fault or blackout, and power degradation from sags and brownouts. A simple formula is
presented for determining the total cost per hour for backup power. Proving power reliability through testing is
recommended and the advantages of three power protection approaches are discussed (standby UPS, power line
conditioners and
backup sources) including minimum requirements for primary and alternate power provided.
Environmental controls are explored in this domain, including the value of positive pressure water drains and climate
monitoring devices used to control temperature, humidity and reduce static electricity. Optimal temperatures and
humidity
settings are provided. Recommendations include strict procedures during emergencies, preventing typical risks (such as
blocked fans), and the use of antistatic armbands and hygrometers. Positive pressurization for proper ventilation and
monitoring for air-born contaminants is stressed.
The pros and cons of several detection response systems are deeply explored in this domain. The concept of
combustion, the classes of fire and fire extinguisher ratings are detailed. Mechanisms behind smoke-activated, heat-activated and
flame-activated devices and Automatic Dial-up alarms are covered, along with their advantages, costs, and
shortcomings. Types of fire sources are distinguished and the effectiveness of fire suppression methods for each is
included. For
instance, Halon and its approved replacements are covered, as are the advantages and the inherent risks to equipment
of the use of water sprinklers.
Administrative controls The physical security domain also deals with administrative controls applied to physical sites and
assets. The need for skilled personnel, knowledge sharing between them, separation of duties, and appropriate
oversight in the care and maintenance of equipment and environments is stressed. A list of management duties
including hiring checks, employee maintenance activities and recommended termination procedures are offered.
Emergency measures include accountability for evacuation and system shutdown procedures, integration with disaster
and business continuity plans, assuring documented procedures are easily available during different types of
emergencies, the scheduling of periodic equipment testing, administrative reviews of documentation, procedures and
recovery plans, responsibilities delegation, and personnel training and drills.
Perimeter security Domain nine also covers the devices and techniques used to control access to space. These
include access control devices, surveillance monitoring, intrusion detection, and corrective actions. Specifications are
provided for optimal external boundary protection, including fence heights and placement, and lighting placement and
types. The selection of door types and lock characteristics are covered. Surveillance methods and intrusion-detection
methods are explained, including the use of video monitoring, guards, dogs, proximity detection systems,
photoelectric/photometric systems, wave pattern devices, passive infrared systems, and sound and motion detectors,
and current flow sensitivity devices that specifically address computer theft. Room lock types — both preset and cipher
locks (and their variations) — device locks, such as portable laptop locks, lockable server bays, switch control locks and
slot locks, port controls, peripheral switch controls, and cable trap locks are also covered. Personal access control
methods used to identify authorized users for site entry are covered at length, noting social engineering risks such as
piggybacking. Wireless proximity devices, both user access and system sensing readers are covered (i.e. transponder
based, passive devices and field powered devices) in this domain.
Now that you\\’ve been introduced to the key concepts of Domain 9, watch the Domain 9, Physical Security video
Return to the CISSP Essentials Security School the main page See all SearchSecurity.com\\’s resources on CISSP
certification training
Source: HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw- Hill/Osborne, 2001, Page 280.
QUESTION 2
Which is a property of a circuit-switched network as opposed to a packet-switched network?
A. Physical, permanent connections exist from one point to another in a circuit-switched network.
B. The data is broken up into packets.
C. Packets are reassembled according to their originally assigned sequence numbers.
D. The data is sent to the next destination, which is based on router\\’s understanding of the best available route.
Correct Answer: A
The correct answer is “Physical, permanent connections exist from one point to another in a circuit-switched network”.
Permanent connections are a feature of circuit-switched networks.
QUESTION 3
Which of the following is the BEST way to determine if a particular system is able to identify malicious software without
executing it?
A. Testing with a Botnet
B. Testing with an EICAR file
C. Executing a binary shellcode
D. Run multiple antivirus programs
Correct Answer: B
QUESTION 4
Which of the following is considered best practice for preventing e-mail spoofing?
A. Spam filtering
B. Cryptographic signature
C. Uniform Resource Locator (URL) filtering
D. Reverse Domain Name Service (DNS) lookup
Correct Answer: B
QUESTION 5
Which is NOT considered a physical intrusion detection method?
A. Wave pattern motion detector
B. Audio motion detector
C. Photoelectric sensor
D. Line supervision
Correct Answer: D
Line supervision is the monitoring of the alarm signaling transmission medium to detect tampering. Audio detectors
monitor a room for any abnormal sound wave generation. Photoelectric sensors receive a beam of light from a light-emitting device. Wave pattern motion detectors generate a wave pattern and send an alarm if the pattern is disturbed.
QUESTION 6
Which of the following statements pertaining to fire suppression systems is TRUE?
A. Halon is today the most common choice as far as an agent is concern because it is highly effective in the way that it
interferes with the chemical reaction of the elements within a fire.
B. Gas masks provide effective protection against the use of CO2 systems. They are recommended for the protection of
the employees within data centers.
C. CO2 systems are NOT effective because they suppress the oxygen supply required to sustain the fire.
D. Water-Based extinguisher are NOT an effective fire suppression method for class C (electrical) fires.
Correct Answer: D
Explanation: Water Based fire extinguishers should never be used on Electrical Fire. If you do so, it will probably the last
time you use such an extinguisher to put out an electrical fire as you will be electrocuted. Any liquid based agent should
be avoided for Electrical Fire.
CO2 systems are effective because they suppress the oxygen supply required to sustain the fire. Since oxygen is
removed, it can be potentially lethal to people and gas masks do not provide protection against CO2. These systems
are more
appropriate for unattended facilities.
The Montreal Protocol of 1987 states that Halon has been designated an ozone-depleting substance and due to the risk
to the environment, production was stopped on January 1st, 1994. Companies that still have Halon systems have been
asked to replace them with nontoxic extinguishers. The name of the agreement is called The Montreal Protocol.
Soda acid is an effective fire suppression method for common combustibles and liquids, but not for electrical fires.
TIP:
Do remember the name of the agreement that was signed in Montreal where countries have agreed to stop production
of Halon, it is called: The Montreal Protocol
A student of mine told me that he thinks about me when he wishes to remember the classes of fire, that scared me off a bit
but his explanations made a lot of sense, here how he is using my first name to remember the classes of fire. My name
is CLEMENT but he is using only the CLEM portion:
C = Common Combustible
L = Liquid Fire
E = Electrical Fire
M = Metals that are flammable
THERE IS ANOTHER WAY TO REMEMBER THEM FROM HARRISON:
A – Ash (common combustible)
B – Bubble/Boil (Liquid)
C – Circuit (Electrical)
D – Metal. (Just remember it 🙂
Reference(s) used for this question:
HARRIS, Shon, All-In-One CISSP Certification Exam Guide, McGraw-Hill/Osborne, 2002, chapter 6: Physical Security
(page 313).
QUESTION 7
Examples of types of physical access controls include all except which of the following?
A. badges
B. locks
C. guards
D. passwords
Correct Answer: D
Explanation: A password is not a physical thing, it\\’s a logical one. You can control physical access with armed guards,
by locking doors and using badges to open doors, but you can\\’t relate password to a physical environment. Just to
remember, Passwords are used to verify that the user of an ID is the owner of the ID. The ID-password combination is
unique to each user and therefore provides a means of holding users accountable for their activity on the system. They
are related to software, not hardware.
QUESTION 8
What attack involves the perpetrator sending a spoofed packet(s) with the SYN flag set to the victim\\’s machine on any
the open port that is listening?
A. Bonk attack
B. Land attack
C. Teardrop attack
D. Smurf attack
Correct Answer: B
Explanation: The Land attack involves the perpetrator sending a spoofed packet(s) with the SYN flag set to the victim\\’s
the machine on any open port that is listening. If the packet(s) contain the same destination and source IP address as the
host,
the victim\\’s machine could hang or reboot.
In addition, most systems experience a total freeze up, whereas CTRL-ALT-DELETE fails to work, the mouse and
keyboard become nonoperational and the only method of correction is to reboot via a reset button on the system or by
turning
the machine off.
Vulnerable Systems:
This will affect almost all Windows 95, Windows NT, Windows for Workgroups systems that are not properly patched
and allow Net Bios over TCP/IP. In addition, machines running services such as HTTP, FTP, Identd, etc that do not
filter
packet(s), that contain the same source/destination IP address, can still be vulnerable to attack through those ports.
Prevention:
This attack can be prevented for open / listening ports by filtering inbound packets containing the same source /
destination IP address at the router or firewall level. For most home users not running a lot of services, and for those
who use
IRC, disabling the Identd server within their client will stop most attacks since the identd service (113) is becoming the
most attacked service/port.
QUESTION 9
Which one of the following is not a primary component or aspect of firewall systems?
A. Protocol filtering
B. Packet switching
C. Rule enforcement engine
D. Extended logging capability
Correct Answer: B
Explanation: This is not the main function of a firewall, packet switching is the main feature of a Switch (working only in
layer 2 of the OSI model). A firewall is a network security device that can function through layer 2 to layer 7 of the OSI
model. They usually include a rule engine that enforces the enterprise security policy of the company. They provide
protocol filtering to enforce our requirements through the forwarded or deny of traffic. They also provide logging
capabilities so we can analyze what is happening at a very low level in our network.
QUESTION 10
An area of the Telecommunications and Network Security domain that directly affects the Information Systems Security
a tenet of Availability can be defined as:
A. Netware availability
B. Network availability
C. Network acceptability
D. Network accountability
Correct Answer: B
Details:
The Answer: Network availability can be defined as an area of the Telecommunications and
Network Security domain that directly affects the Information Systems Security tenet of Availability. Source: KRUTZ,
Ronald L. and VINES, Russel D., The CISSP Prep Guide: Mastering the Ten Domains of Computer Security, 2001,
John Wiley and Sons, Page 64.
QUESTION 11
Which of the following is NOT a characteristic of a distributed data processing (DDP) approach?
A. Consists of multiple processing locations that can provide alternatives for computing in the event of a site becoming
inoperative.
B. Data stored at multiple, geographically separate locations are easily available to the user.
C. Distances from user to processing resources are transparent to the user.
D. Security is enhanced because of networked systems.
Correct Answer: D
Security is more of a concern in distributed systems since there are vulnerabilities associated with the network and the
many locations from which unauthorized access to the computing resources can occur. The other answers are
the characteristics of a DDP architecture.
QUESTION 12
The graph in Figure, which depicts the equation y 2 = x3 + ax + b, denotes the:
Exhibit: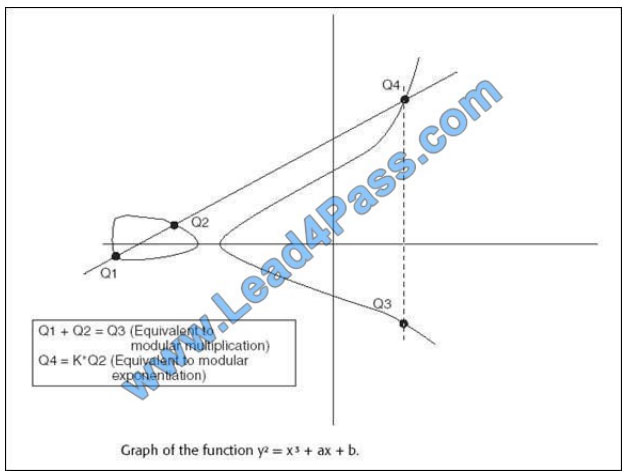
A. RSA Factoring problem
B. Elliptic curve and the elliptic curve discrete logarithm problem
C. ElGamal discrete logarithm problem
D. Knapsack problem
Correct Answer: B
The elliptic curve is defined over a finite field comprised of real, complex or rational numbers. The points on an elliptic
curve form a group under addition. Multiplication (or multiple additions) in an elliptic curve system is equivalent to
modular exponentiation; thus, defining a discreet logarithm problem.
QUESTION 13
What would BEST define a covert channel?
A. An undocumented backdoor that has been left by a programmer in an operating system
B. An open system port that should be closed.
C. A communication channel that allows the transfer of information in a manner that violates the system\\’s security policy.
D. A trojan horse.
CISSP PDF Dumps | CISSP VCE Dumps | CISSP Braindumps 10 / 12
https://www.leads4pass.com/CISSP.html
2020 Latest leads4pass CISSP PDF and VCE dumps Download
Correct Answer: C
Explanation: A covert channel is a way for an entity to receive information in an unauthorized manner. It is an
information flow that is not controlled by a security mechanism. This type of information path was not developed for
communication;
thus, the system does not properly protect this path, because the developers never envisioned information being passed
in this way.
Receiving information in this manner clearly violates the system\\’s security policy. The channel to transfer this
unauthorized data is the result of one of the following conditions:?Oversight in the development of the product
?Improper implementation of access controls
?Existence of a shared resource between the two entities?Installation of a Trojan horse
The following answers are incorrect:
An undocumented backdoor that has been left by a programmer in an operating system is incorrect because it is not a
means by which unauthorized transfer of information takes place. Such backdoor is usually referred to as a
Maintenance
Hook. An open system port that should be closed is incorrect as it does not define a covert channel.
A trojan horse is incorrect because it is a program that looks like a useful program but when you install it would include
a bonus such as a Worm, Backdoor, or some other malware without the installer knowing about it.
Reference(s) used for this question:
Shon Harris AIO v3, Chapter-5: Security Models and Architecture AIOv4 Security Architecture and Design (pages 343
– 344) AIOv5 Security Architecture and Design (pages 345 – 346)
Share leads4pass discount codes for free 2020

leads4pass Reviews
leads4pass offers the latest exam exercise questions for free! ISC exam questions are updated throughout the year.
leads4pass has many professional exam experts! Guaranteed valid passing of the exam! The highest pass rate, the highest cost-effective!
Help you pass the exam easily on your first attempt.

What you need to know:
Latestvce shares the latest ISC Cissp exam dumps,Cissp pdf,Cissp exam exercise questions for free. You can Improve your skills and exam experience online to get complete exam questions and answers guaranteed to pass the exam we recommend leads4pass Cissp exam dumps
Latest update leads4pass Cissp exam dumps: https://www.leads4pass.com/cissp.html (3069 Q&As)
[Q1-Q13 PDF] Free ISC Cissp pdf dumps download from Google Drive: https://drive.google.com/open?id=126N3hMXNUbmXmHWw3T5OGRoE-aJ6vvmI
![SPLK-1003 Dumps Update [2022] for Splunk Core Certified Power User Certification Exam Prepare materials](https://www.latestvce.com/wp-content/themes/blogstream/img/thumb-medium.png)
