
At the end of every year, there will be articles with similar themes such as “The Most Popular Certifications” and “Top Ten Most Popular Certifications” for the next year.
These articles tell you how many of the most popular certifications are available every year, including the CISSP certification I want to share today. Others such as: CompTIA Security+, CEH, CCNP, etc.
So is CISSP really still worth it in 2025?
Worth! Cybersecurity industry profile analysis is expected to reach $79.3 billion by 2032, growing at a CAGR of 14.1% from 2024. And the CISSP certification is the leader in the field of cybersecurity.
This is an expert-level certification for experienced cybersecurity professionals and business leaders looking to advance their careers. CISSP holders hold an average of 18 certifications and tend to hold management positions such as security consultants, IT directors, and chief information security officers. In the United States, those with the CISSP certification earn an average annual salary of $168,060, making it one of the highest-paying IT certifications.
What is CISSP certification?
CISSP (Certified Information Systems Security Professional) is a globally recognized professional certification designed to demonstrate the holder’s knowledge and competence in information systems security.
What are the main advantages of CISSP certification?
Global Recognition: CISSP certification is globally recognized, increasing the credibility and value of certified professionals.
Master Cybersecurity: Demonstrate advanced expertise in information security, covering areas such as risk management and cryptography.
Leadership Opportunities: The CISSP opens doors to cybersecurity management positions, such as Chief Information Security Officer (CISO).
Who issues CISSP certification?
CISSP certification is issued by the International Information Systems Security Certification Consortium (ISC)².
What are the basic requirements to obtain CISSP certification?
Applicants need to have at least five years of full-time work experience, with at least two years of which need to cover two or more domains in the CISSP CBK (Common Body of Knowledge). Certifications are earned after passing the exam and earning an endorsement.
What are the areas covered in the CISSP certification exam?
The CISSP exam covers eight domains: Security and Risk Management, Asset Security, Security Architecture and Engineering, Communications and Network Security, Identity and Access Management, Security Assessment and Testing, Security Operations, and Software Development Security.
What is the time limit for the CISSP certification exam?
The process for obtaining CISSP certification is rigorous. It requires passing a three-hour exam consisting of 100 – 150 questions with at least a 70% answer rate. This demanding certification certifies professionals with proven IT security skills, which are critical in a world of ever-evolving cyber threats.
How long is the CISSP certification valid?
Valid for three years.
How do I maintain the validity of my CISSP certification?
Continuing Professional Education (CPE) credits are earned and submitted
annually and an annual fee is paid.
What is CISSP CBK (Common Body of Knowledge)?
CBK is the body of knowledge covered in the CISSP certification exam, including all aspects of information system security.
Who is suitable for CISSP certification?
Information security professionals, information technology managers, cyber security practitioners, etc.
What kind of work can I do after obtaining CISSP certification?
Information Security Manager, IT Auditor, Security Architect, Information Systems Security Consultant, etc.
How is CISSP certification different from other security certifications (e.g., CEH, CISA)?
CISSP focuses more on comprehensive information security knowledge, while CEH focuses on ethical hacking techniques and CISA focuses on information systems auditing.
What are the differences between the 2024 and 2025 CISSP certification exam questions?
| From | Time | Number of exam questions (Free) | 2025 |
| Leads4Pass | 2024 | 15Q&A | Cissp exam questions |
Question 1:
Which of the following assessment metrics is BEST used to understand a system\’s vulnerability to potential exploits?
A. Determining the probability that the system functions safely during any time period
B. Quantifying the system\’s available services
C. Identifying the number of security flaws within the system
D. Measuring the system\’s integrity in the presence of failure
Correct Answer: C
Question 2:
A manufacturing organization wants to establish a Federated Identity Management (FIM) system with its 20 different supplier companies. Which of the following is the BEST solution for the manufacturing organization?
A. Trusted third-party certification
B. Lightweight Directory Access Protocol (LDAP)
C. Security Assertion Markup language (SAML)
D. Cross-certification
Correct Answer: C
Question 3:
Which of the following BEST represents the concept of least privilege?
A. Access to an object is denied unless access is specifically allowed.
B. Access to an object is only available to the owner.
C. Access to an object is allowed unless it is protected by the information security policy.
D. Access to an object is only allowed to authenticated users via an Access Control List (ACL).
Correct Answer: A
Question 4:
What physical characteristic does a retinal scan biometric device measure?
A. The amount of light reflected by the retina
B. The size, curvature, and shape of the retina
C. The pattern of blood vessels at the back of the eye
D. The pattern of light receptors at the back of the eye
Correct Answer: C
Question 5:
Which of the following is the FIRST requirement a data owner should consider before implementing a data retention policy?
A. Training
B. Legal
C. Business
D. Storage
Correct Answer: B
Question 6:
What principle requires that changes to the plaintext affect many parts of the ciphertext?
A. Diffusion
B. Encapsulation
C. Obfuscation
D. Permutation
Correct Answer: A
Question 7:
The Chief Information Security Officer (CISO) of a large financial institution is responsible for implementing the security controls to protect the confidentiality and integrity of the organization\’s Information Systems. Which of the controls below is prioritized FIRST?
A. Firewall and reverse proxy
B. Web application firewall (WAF) and HyperText Transfer Protocol Secure (HTTPS)
C. Encryption of data in transit and data at rest
D. Firewall and intrusion prevention system (IPS)
Correct Answer: C
Question 8:
Which of the following is the MOST important reason for timely installation of software patches?
A. Attackers may be conducting network analysis.
B. Patches ere only available for a specific time.
C. Attackers reverse engineer the exploit from the patch.
D. Patches may not be compatible with proprietary software
Correct Answer: C
Question 9:
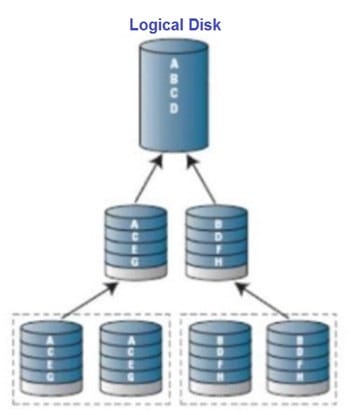
Which Redundant Array of Independent Disks (RAID) Level does the following diagram represent?
A. RAID 0
B. RAID 1
C. RAID 5
D. RAID 10
Correct Answer: D
Question 10:
A system with Internet Protocol (IP) address 10.102.10.2 has a physical address of 00:00:08:00:12:13:14:2f. The following static entry is added to its Address Resolution Protocol (ARP) table: 10.102.10.6: 00:00:08:00:12:13:14:2f.
What form of attack could this represent?
A. A Denial of Service (DoS) attack against the gateway router because the router can no longer accept packets from 10.102.10.2
B. A transport layer attack that prevents the resolution of 10.102.10.6 address
C. A Denial of Service (DoS) attack against 10.102.10.2 because it cannot respond correctly to ARP requests
D. A masquerading attack that sends packets intended for 10.102.10.6 to 10.102.10.2
Correct Answer: D
Question 11:
The use of private and public encryption keys is fondamental in the implementation of which of the following?
A. Diffie-Hellman algorithm
B. Message Digest 5 (ND5)
C. Secure Sockets Layer (SSL)
D. Advanced Encryption Standard (AES)
Correct Answer: C
Question 12:
An organization allows ping traffic into and out of their network. An attacker has installed a program on the network that uses the payload portion of the ping packet to move data into and out of the network. What type of attack has the organization experienced?
A. Data leakage
B. Unfiltered channel
C. Data emanation
D. Covert channel
Correct Answer: D
Question 13:
Who is responsible for the protection of information when it is shared with or provided to other organizations?
A. Systems owner
B. Authorizing Official (AO)
C. Information owner
D. Security officer
Correct Answer: C
Question 14:
A security professional can BEST mitigate the risk of using a Commercial Off-The-Shelf (COTS) solution by deploying the application with which of the following controls in ?
A. Whitelisting application
B. Network segmentation
C. Hardened configuration
D. Blacklisting application
Correct Answer: A
Question 15:
Which concept might require users to use a second access token or to re-enter passwords to gain elevated access rights in the identity and access provisioning life cycle?
A. Time-based
B. Enrollment
C. Least privilege
D. Access review
Correct Answer: B
…
2025 Cissp exam questions and answers
Is the CISSP certification still worth it in 2025? What changes will happen to the certification exam in 2025? Follow Leads4Pass!
Leads4Pass real-time updates provide the latest Cissp exam questions and answers. https://www.leads4pass.com/cissp.html There are currently 1,703 exam questions and answers available to ensure you successfully pass the exam.

